So.. I have had ovh for a while now and this has never happend before, I am running ubuntu 20.04
Just wondering if somebody else has gotten these mails from them? This resulted in my server shutting down but luckily I had backups.. As I just thought they were SPAM
BLACKEDOUT are just my IP for my server!
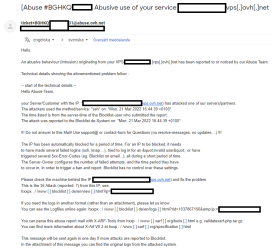
Just wondering if somebody else has gotten these mails from them? This resulted in my server shutting down but luckily I had backups.. As I just thought they were SPAM
BLACKEDOUT are just my IP for my server!