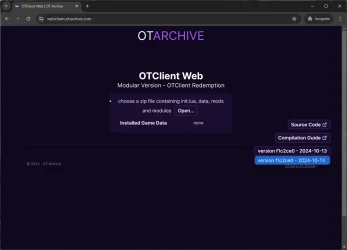
OT Archive
Advanced OT User
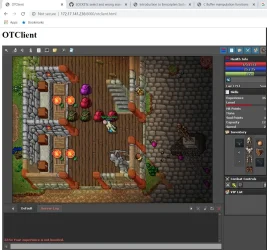
OTClient Redemption (mehah) for Web Browsers
I've adapted OTClient Redemption to run on browsers:
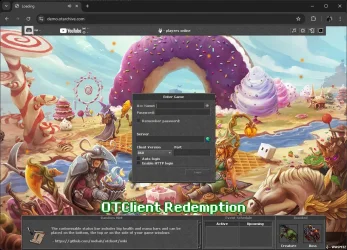
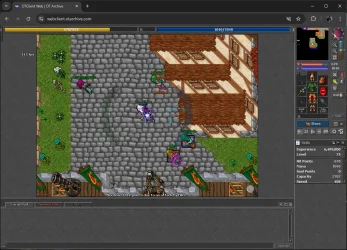
@Gesior.pl was the first to add support to a real server:
I've adapted OTClient Redemption to run on browsers:


@Gesior.pl was the first to add support to a real server:
I setup nginx+websockify like this:
444 -> 7171
443 -> 7172
In client set port to login to 444 and inmodules/client_entergame/characterlist.luaforced it to use proxy address"web.skalski.pro":
LUA:g_game.loginWorld(G.account, G.password, charInfo.worldName, "web.skalski.pro", charInfo.worldPort, charInfo.characterName, G.authenticatorToken, G.sessionKey)
I've updated my client files on host, you can use this URL to start client that logins toarm.skalski.proThaisWar with bots 8.6 OTS:
Login/password:Code:https://webclient.otarchive.com/?gameData=https://downloads-oracle.ots.me/data/MehahWeb860/otclient-otarchive.zipppp/ppp(many people use this and kick other players from this account characters)
You can create own account: Createaccount - Forgotten (https://arm.skalski.pro/?subtopic=createaccount)
It would be much easier to use with WS, not WSS. You could use IP, not domain and it would not require generating SSL certificates.
I use nginx proxy to offload SSL now. After changing to WS, I could use just websockify.
Tibia protocol itself is encrypted with XTEA, packets containing user login/password are encrypted using RSA.
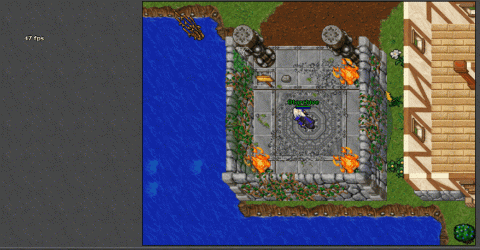
View attachment 87536
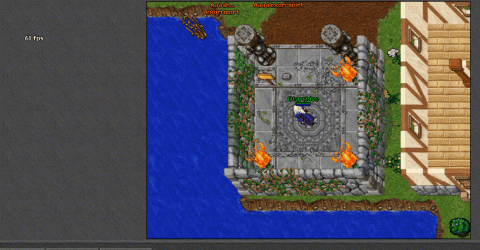
View attachment 87537
nginx config:
Code:server { server_name web.skalski.pro; location / { proxy_pass http://localhost:7172; proxy_set_header X-Real-IP $remote_addr; proxy_set_header Host $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # WebSocket support proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } listen [::]:443 ssl ipv6only=on; # managed by Certbot listen 443 ssl; # managed by Certbot ssl_certificate /etc/letsencrypt/live/web.skalski.pro/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/web.skalski.pro/privkey.pem; # managed by Certbot include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot } server { server_name web.skalski.pro; location / { proxy_pass http://localhost:7171; proxy_set_header X-Real-IP $remote_addr; proxy_set_header Host $host; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; # WebSocket support proxy_http_version 1.1; proxy_set_header Upgrade $http_upgrade; proxy_set_header Connection "upgrade"; } listen [::]:444 ssl ipv6only=on; # managed by Certbot listen 444 ssl; # managed by Certbot ssl_certificate /etc/letsencrypt/live/web.skalski.pro/fullchain.pem; # managed by Certbot ssl_certificate_key /etc/letsencrypt/live/web.skalski.pro/privkey.pem; # managed by Certbot include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot }
Last edited: