Hey, what's up?
The goal of this list is to help you protect and improve the security of your webserver. This guide is generic, it works for any webserver, but some of them are more OTServ related.
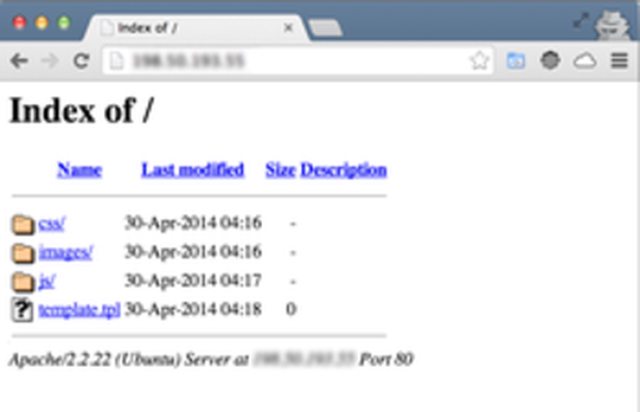
To turn off directory listing, you should follow 3 steps:
To remove server tokens, you will follow 3 steps too:
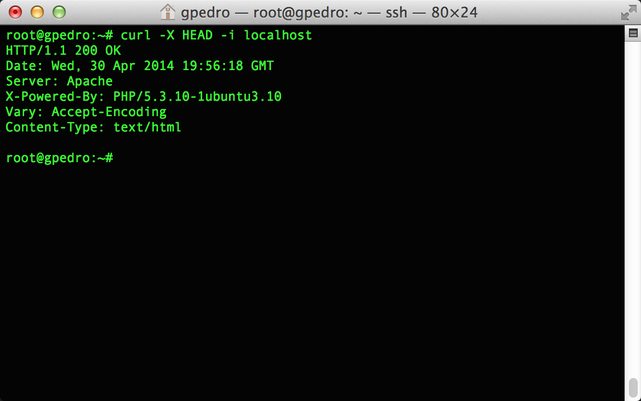
When we make a request to a page interpreted with PHP, by default, on the headers of the response it is possible to identify the PHP version, and it's better to turn it off since those important data should not be exposed. Only 3 steps (side note: I swear it's the last time) should be followed to solve this problem.

Translation: "STOP THIS S***, MATE!! YOU WERE RAISED WITH MILK AND PEAR! WITH OVALTINE! BREAD WITH MORTADELLA! JUVENILE BOY, YOU CAN'T HANDLE TEN MINUTES OF FIGHT WITH ME! YOU SON OF A B****!!!"
You must have complete control over what is installed or not and don't use those crappy bundles. You should install and configure the packages individually with care.
Except Baidu, it always come bundled.

The biggest servers use it to have full control of the files. On every update, it creates a new revision of the files. You can edit millions of times and see what changed, who changed, what was added and removed. Its beautiful.
Read about SVN and Git, they are excellent tools.
This guide was created by Gabriel Pedro (gpedro) and posted on http://forums.otserv.com.br/index.php/topic/165027-10-dicas-de-segurança-para-seu-servidor-web/ (portuguese)
The goal of this list is to help you protect and improve the security of your webserver. This guide is generic, it works for any webserver, but some of them are more OTServ related.
-----------------

Directory Listing
It is a common and severe mistake, since it is possible to retrieve relevant data for a potential weakness abuse, vulnerabilities and even information stealing.To turn off directory listing, you should follow 3 steps:
- Browse to /etc/apache2/sites-enabled and open 000-default
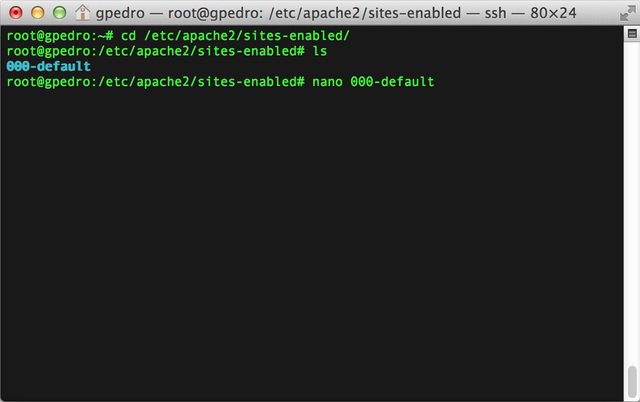
I am using nano, a terminal-based text editor.
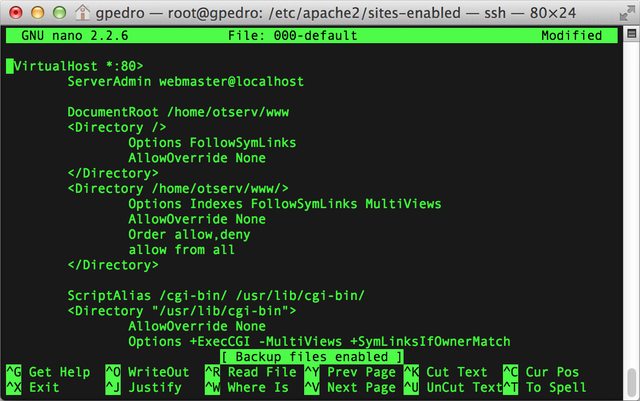
- Search for the line <Directory /path/to/www>, where /path/to/www means your document directory for Apache. Look for Options Indexes and change it to Options -Indexes (add a hyphen)
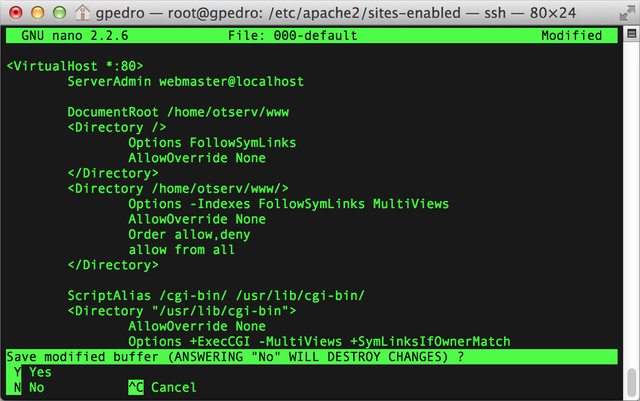
Then save and close the file.
- Now we need to restart the Apache service for the configurations take place. In the terminal, execute service apache2 restart
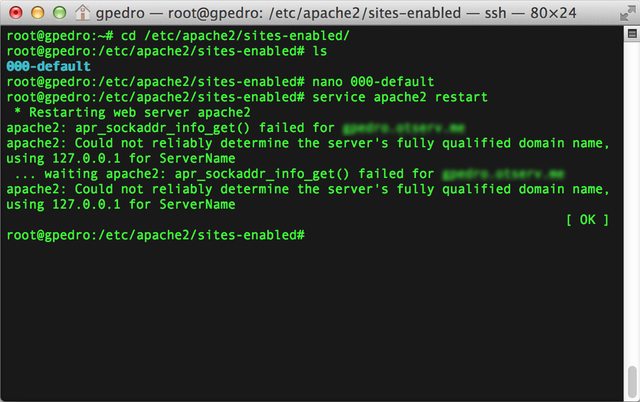
Result (before and after):
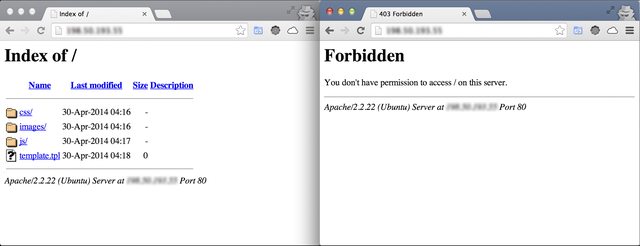

-----------------
Server Tokens
If you see the image above, you will see that we reduced the amount of internal files data, but if you look closely at the bottom, in the page footer, it is written all our webserver infrastructure, in other words, I'm using Apache 2.2.22 on an Ubuntu. This is not good to expose, because if one knows the software version it is possible to search for exploits already found of those specific versions.To remove server tokens, you will follow 3 steps too:
- Browse to /etc/apache2/conf.d and open security
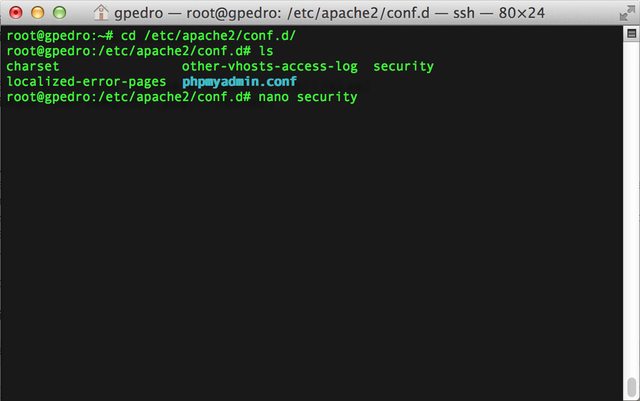
- On the top lines, you will see two attributes we must change, ServerTokens and ServerSignature, where we must change the values to Prod and Off respectively.
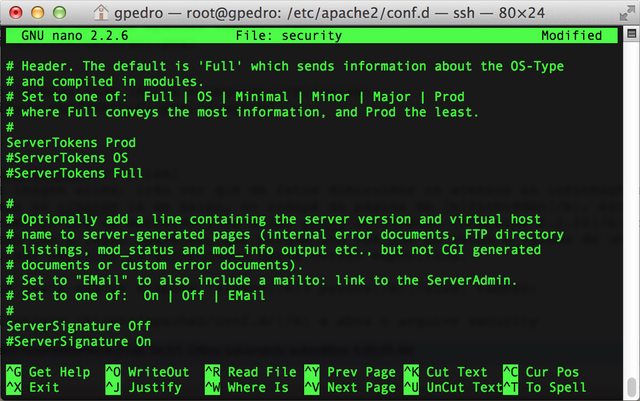
- After that, save the file and restart Apache as mentioned previously.
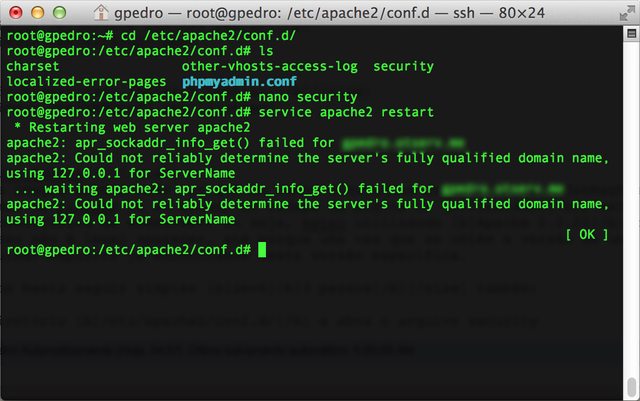
Result:
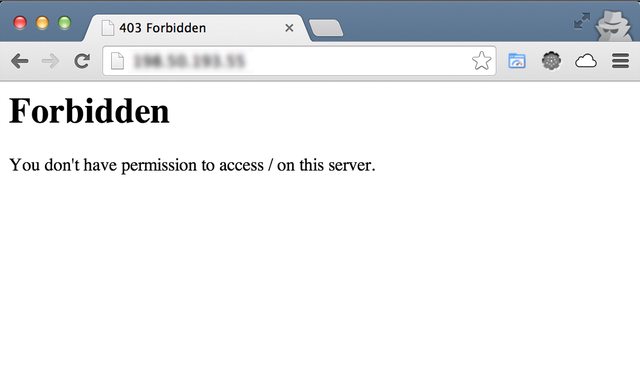

-----------------

Expose PHP
When we make a request to a page interpreted with PHP, by default, on the headers of the response it is possible to identify the PHP version, and it's better to turn it off since those important data should not be exposed. Only 3 steps (side note: I swear it's the last time) should be followed to solve this problem.
- Browse to /etc/php5/apache2 and open php.ini
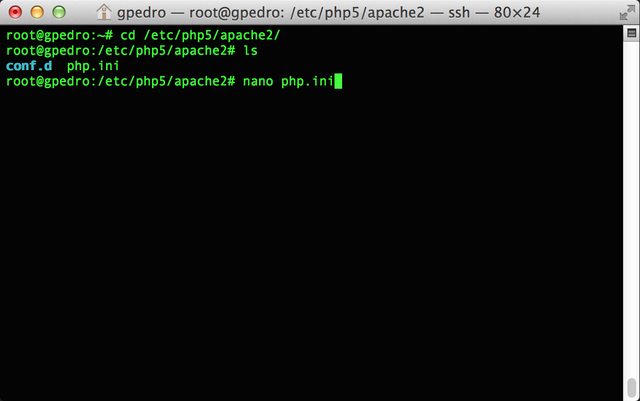
- Search for the attribute expose_php and change it from On to Off
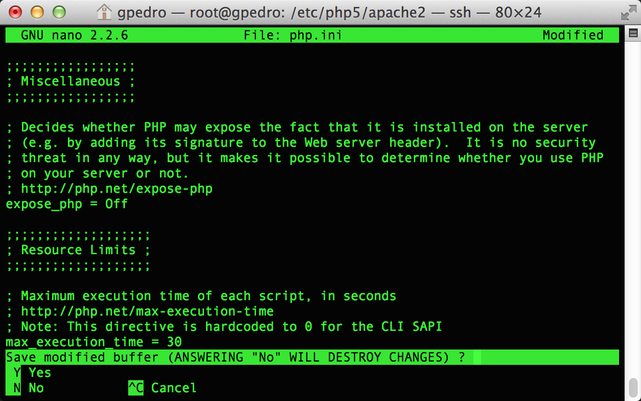
- Save the file and restart Apache.
Result

-----------------
Unneeded files
When we implement a script we do not have knowledge to do or it has a lot of dependencies, we usually download the documentation and example files to read and then implement. But it sometimes happen after we implement and it works, we forget the documentation and examples there. It is not only developers' fault, no, it happens with curious users too. A good example is Gesior AAC, where we create out pages, include them on index.php and post the modification, then someone that does not use it just removes from the layout and thinks everything is removed. The hole is much deeper.-----------------
High priority defect solved in a messy way
Put like this it seems to be advanced, magnificent, but it is simply a workaround or hardcoded ugly hack. Those modifications or implementations in a very amateur way may open breaches in the security of our website. So, when you want to implement something correctly, search for someone with advanced knowledge of a professional, read the manuals of the language and the framework used.-----------------
Keep everything up-to-date
Be it software or infrastructure, keep it updated. It is extremely necessary. Do you still want a good reason to do it? Recently, a flaw was found on every version of Internet Explorer (side note: I hope you are not using it) that could hand the hacker almost full access to your system. And it was just found and fixed a week ago.-----------------
Default passwords
Please people, do change every default password. Change them to secure ones, and by secure I mean admin, 12345 and test are out. A secure password involves numbers, letters - both lower and uppercase -, a special character and at leasr 6 digits.-----------------
A kilogram of shame in your face
"Oh well, it's a Linux server, I will just install XAMPP..."
Translation: "STOP THIS S***, MATE!! YOU WERE RAISED WITH MILK AND PEAR! WITH OVALTINE! BREAD WITH MORTADELLA! JUVENILE BOY, YOU CAN'T HANDLE TEN MINUTES OF FIGHT WITH ME! YOU SON OF A B****!!!"
You must have complete control over what is installed or not and don't use those crappy bundles. You should install and configure the packages individually with care.
-----------------
WebDAV
Last year, there were a lot of people suffering with this. A flaw in XAMPP, that started WebDAV with a default password, let anyone come, access your machine and make a mess. This is to reforce the above point, since you will only install the needed. -----------------
Control Version System
That's the deal. Who never accidentally deleted part of a file in the text editor and saved, then the modification did not work and you cound not undo?
The biggest servers use it to have full control of the files. On every update, it creates a new revision of the files. You can edit millions of times and see what changed, who changed, what was added and removed. Its beautiful.
Read about SVN and Git, they are excellent tools.
-----------------
References
- http://wiki.apache.org/httpd/DirectoryListings#Directory_Listings
- http://httpd.apache.org/docs/current/pt-br/mod/core.html#servertokens
- http://httpd.apache.org/docs/current/pt-br/mod/core.html#serversignature
- http://www.php.net/manual/en/ini.core.php#ini.expose-php
- https://www.acunetix.com/websitesecurity/webserver-security/
- http://wikipedia.org/wiki/Hard_code
- http://www.zdnet.com/blog/security/25-most-used-passwords-revealed-is-yours-one-of-them/12427
- http://www.apachefriends.org/f/viewtopic.php?f=16&t=44140#p172246
- http://svnbook.red-bean.com/en/1.7/index.html
- http://git-scm.com/book
This guide was created by Gabriel Pedro (gpedro) and posted on http://forums.otserv.com.br/index.php/topic/165027-10-dicas-de-segurança-para-seu-servidor-web/ (portuguese)
