Discovery
Developing myself
Hi fellow CPU abusers and byte fans,
Today I found something who people ask me about traffic filters, ddos, and load balancers in modern applications.
The knowledge about DNS can solve your issues with players connection, and improve the quality between user->server (web, login, game servers).
The repository containing all this information is available on my for fork, and original wrote by DonneMartin (github).
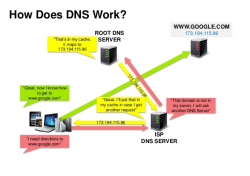
Domain name system (D N S)
A Domain Name System (DNS) translates a domain name such as www.example.com to an IP address.
DNS is hierarchical, with a few authoritative servers at the top level. Your router or ISP provides information about which DNS server(s) to contact when doing a lookup. Lower level DNS servers cache mappings, which could become stale due to DNS propagation delays. DNS results can also be cached by your browser or OS for a certain period of time, determined by the time to live (TTL).

Today I found something who people ask me about traffic filters, ddos, and load balancers in modern applications.
The knowledge about DNS can solve your issues with players connection, and improve the quality between user->server (web, login, game servers).
The repository containing all this information is available on my for fork, and original wrote by DonneMartin (github).
Domain name system (D N S)
A Domain Name System (DNS) translates a domain name such as www.example.com to an IP address.
DNS is hierarchical, with a few authoritative servers at the top level. Your router or ISP provides information about which DNS server(s) to contact when doing a lookup. Lower level DNS servers cache mappings, which could become stale due to DNS propagation delays. DNS results can also be cached by your browser or OS for a certain period of time, determined by the time to live (TTL).
- NS record (name server) - Specifies the DNS servers for your domain/subdomain.
- MX record (mail exchange) - Specifies the mail servers for accepting messages.
- A record (address) - Points a name to an IP address.
- CNAME (canonical) - Points a name to another name or CNAME (example.com to www.example.com) or to an A record.
- Weighted round robin
- Prevent traffic from going to servers under maintenance
- Balance between varying cluster sizes
- A/B testing
- Latency-based
- Geolocation-based
- Accessing a DNS server introduces a slight delay, although mitigated by caching.
- DNS server management could be complex and is generally managed by governments, ISPs, and large companies.
- DNS services have recently come under DDoS attack, preventing users from accessing websites such as Twitter without knowing Twitter's IP address(es).

Attachments
-
 1590601677356.png92.4 KB · Views: 4 · VirusTotal
1590601677356.png92.4 KB · Views: 4 · VirusTotal
Last edited: