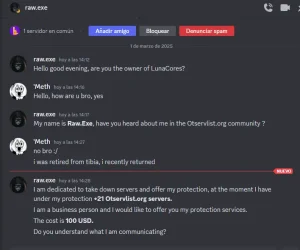
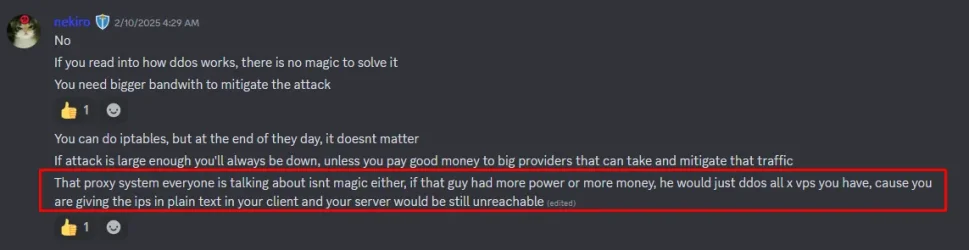
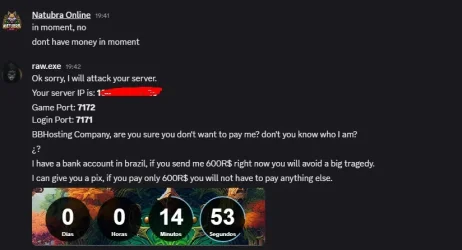
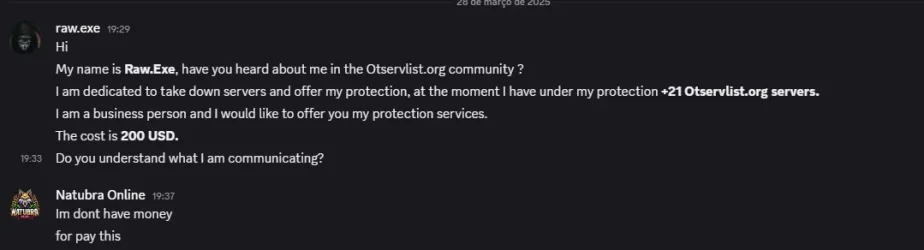
he is actually smart for me on exoria it was different, he tried to do bruteforce ssh attacks which cause denial of service for 5-15 seconds for the servers he could find its ip, i would say he isn't even skilled enough to trace what he is connecting to, he just checks domain, ip on otservlist so i did the following:
1) setup otclientv8 to connect to any of the available proxies through the known 127.0.0.1: proxyPort configuration (login & game)
2) seperate status server from login (otservlist sniffs status information alone from the server on specific port) : so even if it is attacked, you don't lose connection in game, whitelist otservlist on that server and block all (ask xinn for allowance to do that), he is cooperative if you have clean reputation so he will share what he can.
3) using multiple proxy with service provider firewall on hash rate on your custom ips (ban countries that know nothing about tibia as well)
4) reduce connection re-establishment from proxy_client.cpp or proxy.cpp (can't recall the file name) from 2500 to something smaller like 500 (which is still unplayable) and there was another value setted to 500 i changed to 250 (no details here i will have to explain much so either send the files to an AI to explain those defined values roles or make the change as instructed.
5) make sure your main server ONLY allows connection to your known channels (proxy servers, web server)
6) cloudflare is necessary for website and good apache2 configuration (credits to gesior to inform me about that earlier on my first attack occurance
@Gesior.pl)
I want to make sure that you know you have to limit connections per ip, limit hash rate, don't make it lower than your server so players doesn't disconnect every 10mins .. etc, iptables is useless the attacks are huge enough so as long as your iptables on the unix level is going to start treating them they will cause ddos, it have to be service provider iptables (main provider ethernet firewall not your server firewall) another layer of your server fire wall would require fail2ban
Finally never use 22 for ssh or 21 for ftp that just makes you threatened by kids
Following that i could sleep at night without worrying about servers monitoring
So you need proxies for sure and you can do something smart like load balancers for multi proxies on the same region if 1 proxy won't be able to handle the connection (which won't happen before that single proxy is serving 500+ players which in tibia a very rare occurance)
I use 4 proxies and another 4 proxies ready to replace them on the same DNS if anything weong happened that its not pinging through simple shell code in linux on cron