- Joined
- Jul 12, 2008
- Messages
- 267
- Solutions
- 13
- Reaction score
- 438
- Location
- Bialystok, Poland
- GitHub
- rookgaard
- YouTube
- Rookgaard
Hello.
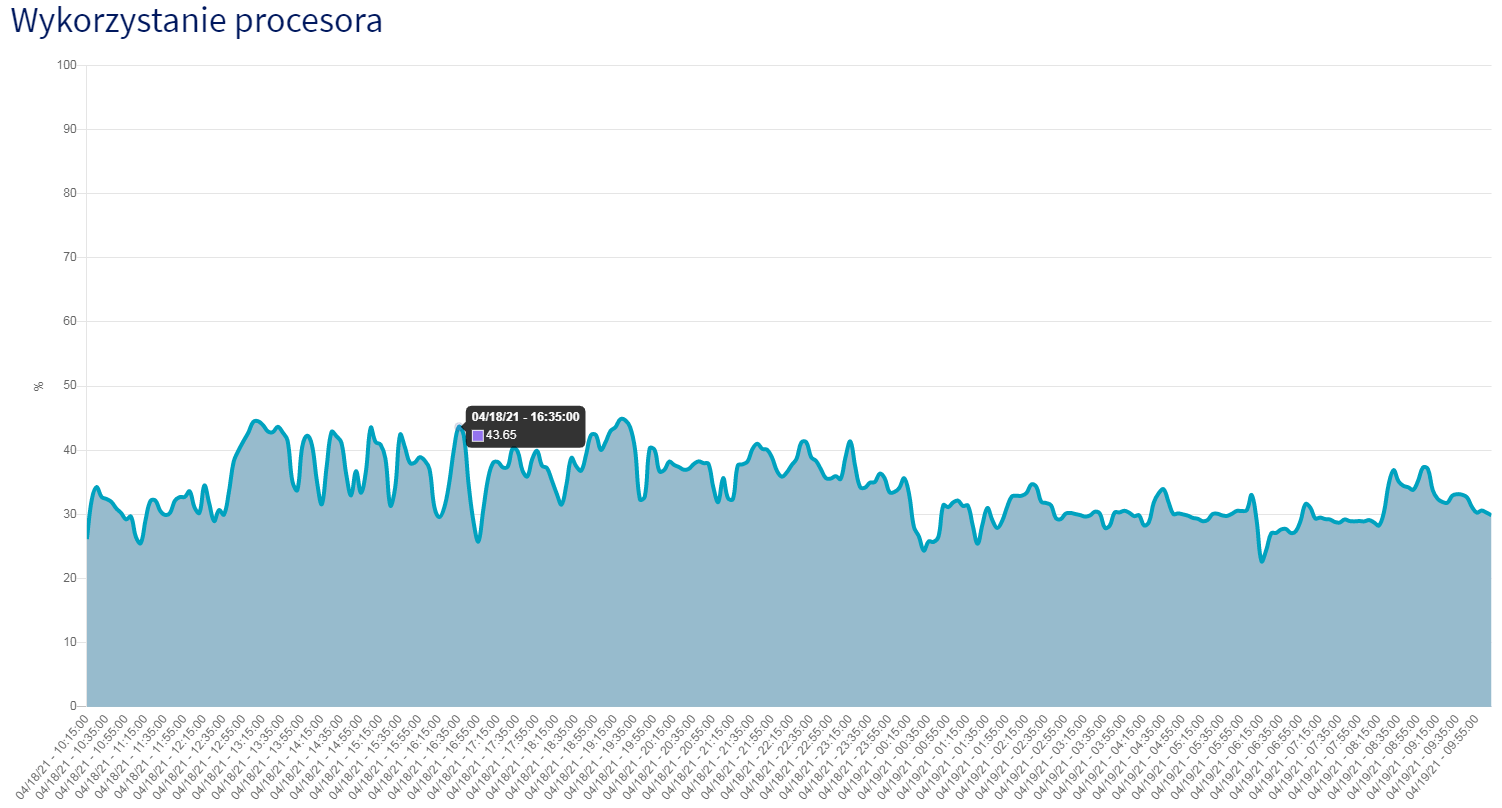
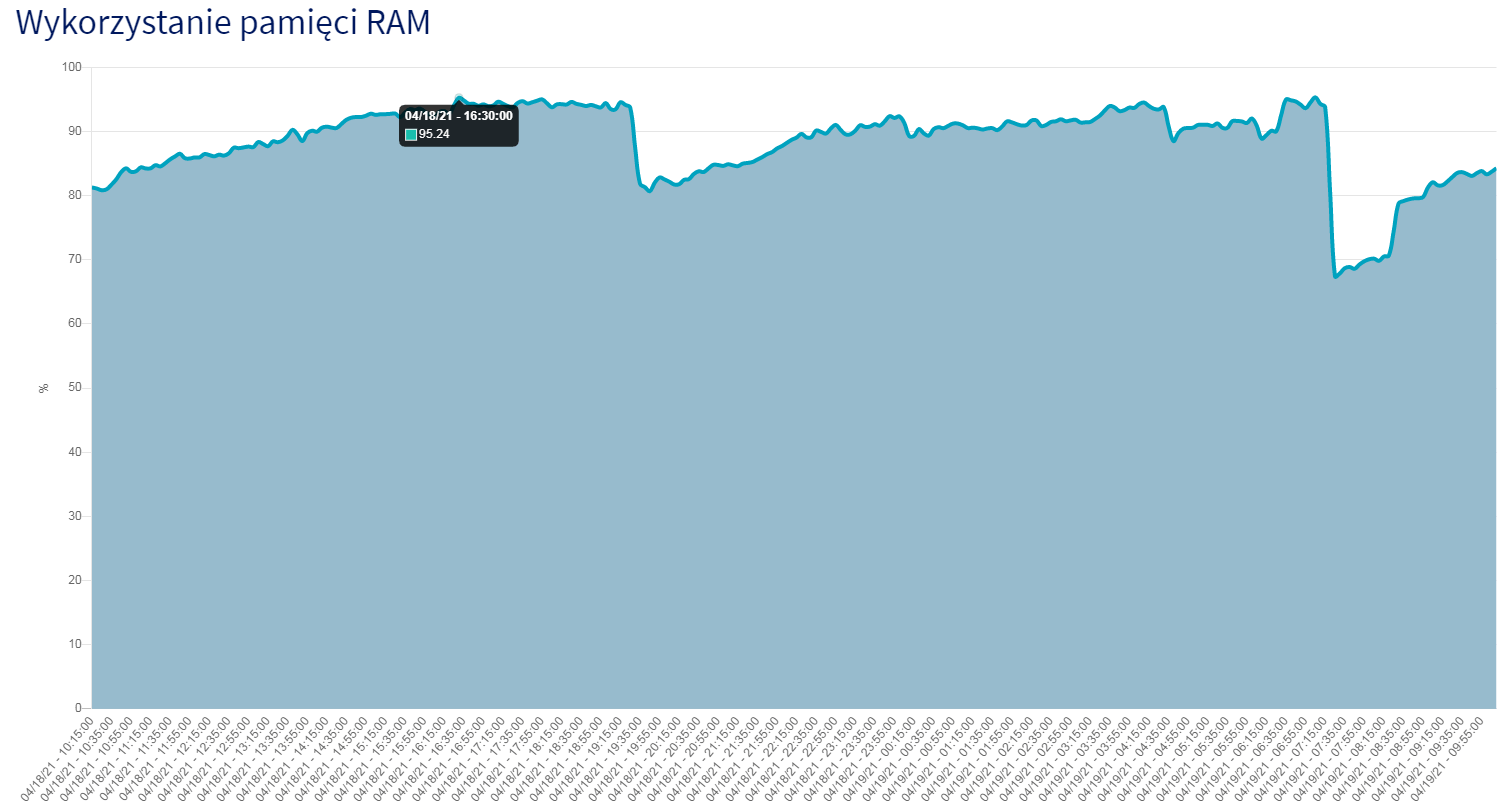
On my 5 years old server first time I meet a crash (5x just today) which I'm not able to fix (and even find a reason) on my own. It's probably a deliberate action as it happened in quick succession without any connection with globalevent (such as server save or other quests scripts) or other logged in player's action (I have a system which records theirs incoming and outgoing packets) - looks like it's some already prepared data sent to gameserver port.
OS: 16.04.6 LTS (Xenial Xerus)
boost: 1.58.0.1ubuntu1
TFS: Fir3element/3777 (https://github.com/Fir3element/3777) with
Here's a list what console recorded and what gdb output was:
Crash no. 1 at 2021-04-18 16:24:13
console: just
gdb: gdb tfs0 core-2021-04-18-16-24-13-356567362GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/Jg4cJqTE)
Crash no. 2 at 2021-04-18 16:31:40
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001239c80 ***=== - Pastebin.com (https://pastebin.com/s7F2cN10)
gdb: gdb tfs0 core-2021-04-18-16-31-40-910861589GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/HaLWMbjC)
Crash no. 3 at 2021-04-18 16:32:59
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x00000000027463a0 ***=== - Pastebin.com (https://pastebin.com/U3xHkG1K)
gdb: gdb tfs0 core-2021-04-18-16-32-59-695611728GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/at2z8sSF)
Crash no. 4 at 2021-04-18 17:28:58
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001e7ff70 ***=== - Pastebin.com (https://pastebin.com/EZHGRjvE)
gdb: gdb tfs0 core-2021-04-18-17-28-58-369723171GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/SmnSP8qd)
Crash no. 5 at 2021-04-18 17:45:56
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001742ad0 ***=== - Pastebin.com (https://pastebin.com/Hdqhmyaw)
gdb: gdb tfs0 core-2021-04-18-17-45-56-866334916GNU gdb (Ubuntu 7.11.1-0ubuntu1~16 - Pastebin.com (https://pastebin.com/pvXv7Ska)
Is there someone who can help me find what happened? Or just where to put some logging incoming IP or something else?
Thanks,
Michal "Gubihe"
On my 5 years old server first time I meet a crash (5x just today) which I'm not able to fix (and even find a reason) on my own. It's probably a deliberate action as it happened in quick succession without any connection with globalevent (such as server save or other quests scripts) or other logged in player's action (I have a system which records theirs incoming and outgoing packets) - looks like it's some already prepared data sent to gameserver port.
OS: 16.04.6 LTS (Xenial Xerus)
boost: 1.58.0.1ubuntu1
TFS: Fir3element/3777 (https://github.com/Fir3element/3777) with
debugBuild=yes in Fir3element/3777 (https://github.com/Fir3element/3777/blob/master/src/configure.ac#L74)Here's a list what console recorded and what gdb output was:
Crash no. 1 at 2021-04-18 16:24:13
console: just
Segmentation fault (core dumped)gdb: gdb tfs0 core-2021-04-18-16-24-13-356567362GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/Jg4cJqTE)
Crash no. 2 at 2021-04-18 16:31:40
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001239c80 ***=== - Pastebin.com (https://pastebin.com/s7F2cN10)
gdb: gdb tfs0 core-2021-04-18-16-31-40-910861589GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/HaLWMbjC)
Crash no. 3 at 2021-04-18 16:32:59
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x00000000027463a0 ***=== - Pastebin.com (https://pastebin.com/U3xHkG1K)
gdb: gdb tfs0 core-2021-04-18-16-32-59-695611728GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/at2z8sSF)
Crash no. 4 at 2021-04-18 17:28:58
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001e7ff70 ***=== - Pastebin.com (https://pastebin.com/EZHGRjvE)
gdb: gdb tfs0 core-2021-04-18-17-28-58-369723171GNU gdb (Ubuntu 7.11.1-0ubuntu1~16. - Pastebin.com (https://pastebin.com/SmnSP8qd)
Crash no. 5 at 2021-04-18 17:45:56
console: *** Error in `./tfs0': corrupted size vs. prev_size: 0x0000000001742ad0 ***=== - Pastebin.com (https://pastebin.com/Hdqhmyaw)
gdb: gdb tfs0 core-2021-04-18-17-45-56-866334916GNU gdb (Ubuntu 7.11.1-0ubuntu1~16 - Pastebin.com (https://pastebin.com/pvXv7Ska)
Is there someone who can help me find what happened? Or just where to put some logging incoming IP or something else?
Thanks,
Michal "Gubihe"