hello, some one hacked my website, take points 100000-Deleted Adm, Give self Access 5
gesior 2012 Full bug
gesior 2012 Full bug
Attachments
-
 Untitled.png357.7 KB · Views: 66 · VirusTotal
Untitled.png357.7 KB · Views: 66 · VirusTotal

He found 1 hack he knew. You can ask/pay him, so he will tell you how to fix it on priv.what

yeah, looks like you don't want help.never, i`m have port code in my ip
no one can hack vps
go test
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1" />
<?PHP
if($logged) {
if ($action == '') {
$main_content .= '<center>Here is the list of the current characters that are in the shop!</center>';
$main_content .= '<BR>';
$main_content .= '<TABLE BORDER=1 CELLSPACING=1 CELLPADDING=4 WIDTH=100%><TR BGCOLOR='.$config['site']['vdarkborder'].'><TD CLASS=white width="64px"><CENTER><B>Name</B></CENTER></TD><TD CLASS=white width="64px"><CENTER><B>Vocation</B></CENTER></TD><TD CLASS=white width="64px"><CENTER><B>reset</B></CENTER></TD><TD CLASS=white width="64px"><CENTER><B>Price</B></CENTER></TD><TD CLASS=white width="64px"><CENTER><B>Buy it</B></CENTER></TD></TR>';
$getall = $SQL->query('SELECT `id`, `name`, `price`, `status` FROM `sellchar` ORDER BY `id`')or die(mysql_error());
foreach ($getall as $tt) {
$namer = $tt['name'];
$queryt = $SQL->query("SELECT `name`, `vocation`, `reset` FROM `players` WHERE `name` = '$namer'");
foreach ($queryt as $ty) {
if ($ty['vocation'] == 1) {
$tu = 'Sorcerer';
} else if ($ty['vocation'] == 2) {
$tu = 'Druid';
} else if ($ty['vocation'] == 3) {
$tu = 'Paladin';
} else if ($ty['vocation'] == 4) {
$tu = 'Knight';
} else if ($ty['vocation'] == 5) {
$tu = 'Sorcerer';
} else if ($ty['vocation'] == 6) {
$tu = 'Druid';
} else if ($ty['vocation'] == 7) {
$tu = 'Paladin';
} else if ($ty['vocation'] == 8) {
$tu = 'Knight';
}
$ee = $tt['name'];
$ii = $tt['price'];
$main_content .= '<TR BGCOLOR='.$config['site']['darkborder'].'><TD CLASS=black width="64px"><CENTER><B><a href="index.php?subtopic=characters&name='.$tt['name'].'">'.$tt['name'].'</a></B></CENTER></TD><TD CLASS=black width="64px"><CENTER><B>'.$tu.'</B></CENTER></TD><TD CLASS=black width="64px"><CENTER><B>'.$ty['reset'].'</B></CENTER></TD><TD CLASS=black width="64px"><CENTER><B>'.$tt['price'].'</B></CENTER></TD><TD CLASS=black width="64px"><CENTER><B>
<form action="?subtopic=buychar&action=buy" method="POST">
<input type="hidden" name="char" value="'.$ee.'">
<input type="hidden" name="price" value="'.$ii.'">
<input type="submit" name="submit" value="Buy it"></B></CENTER></TD></TR></form>';
}
}
$main_content .= '</TABLE>';
}
if ($action == 'buy') {
$name = $_POST['char'];
$price = $_POST['price'];
$ceh = $SQL->query("SELECT `name` FROM `sellchar` WHERE `name` = '$name'");
if ($ceh) {
if ($name == '') {
$main_content .= '<b><center>Select a character to buy first/b>';
} else {
$user_premium_points = $account_logged->getCustomField('premium_points');
$user_id = $account_logged->getCustomField('id');
if ($user_premium_points >= $price) {
$check = $SQL->query("SELECT * FROM `sellchar` WHERE `name` = '$name'") or die(mysql_error());
$check1 = $SQL->query("SELECT * FROM `players` WHERE `name` = '$name'") or die(mysql_error());
$check2 = $SQL->query("SELECT `oldid` FROM `sellchar` WHERE `name` = '$name'");
foreach ($check as $result) {
foreach($check1 as $res) {
foreach($check2 as $ress) {
$oid = $ress['oldid'];
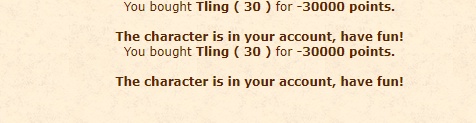
$main_content .= '<center>You bought<b> '.$name.' ( '.$res['reset'].' ) </b>for <b>'.$result['price'].' points.</b><br></center>';
$main_content .= '<br>';
$main_content .= '<center><b>The character is in your account, have fun!</b></center>';
$execute1 = $SQL->query("UPDATE `accounts` SET `premium_points` = `premium_points` - '$price' WHERE `id` = '$user_id'");
$execute2 = $SQL->query("UPDATE `players` SET `account_id` = '$user_id' WHERE `name` = '$name'");
$execute2 = $SQL->query("UPDATE `accounts` SET `premium_points` = `premium_points` + '$price' WHERE `id` = '$oid'");
$execute3 = $SQL->query("DELETE FROM `sellchar` WHERE `name` = '$name'");
}
}
}
} else {
$main_content .= '<center><b>You dont have enought premium points</b></center>';
}
}
} else {
$main_content .= '<center><b>Character cannot be buyed</b></center>';
}
}
} else {
$main_content .= '<center>Please log in first!</center>';
}
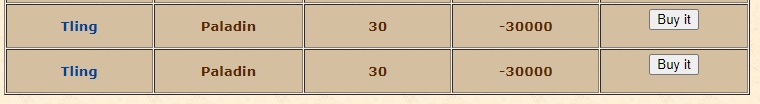
?>yes, you can put 2x the same character if you set the negative value to it.I just confirm it, its the characters auction.
Anyways you should do what Gesior suggested

I haven't noticed it's VPS, not home PC. XAMPP made my think it's home PC.never, i`m have port code in my ip
no one can hack vps
go test
iptables to tell Linux to block specific actions:
Nice@Joker Man

[Gesior ACC] Buy / sell characters
These scripts do work, but they are so easy to exploit. By 1 simple edit client side I managed to sell a a char on the main account, for 0 coins on a fresh account then buy it on it thus transferring to my new account. You can also put a char up for sale at 10000 points, and buy it for 1 point...otland.net
Sorry my brother, i have full protc, like Shield for any ddosI haven't noticed it's VPS, not home PC. XAMPP made my think it's home PC.
Maybe no one can hack Windows VPS, but any internet user can DDoS it using 1 mb/s connection and it will go down. It's Windows.
Even Microsoft hosts THEIR sites on Linux.
Open 10k connections in same time? Send 10k requests to www? Windows will go down. Good luck looking for Windows firewall that will detect simple attacks like that and block them.
NiceI've forgotten about that bug.
You also had OTS that was not hackable, until someone hacked it.Sorry my brother, i have full protc, like Shield for any ddos
vps like 20$
nginx - Apache replacement, easy to install on Linux - in 2012 Xampp - ataki (https://otland.net/threads/xampp-ataki.175332/) (https://www.google.com/search?q=xampp+slowloris).What distro of linux do you recommend? I'm a linux virgin. So I need one that has a lot of support/info. I just got everything working and compiled on windows. And now I want to cry lol.You also had OTS that was not hackable, until someone hacked it.
Datacenter DDoS protection may protect you from basic DDoSes (only OVH anti-ddos does it! other datacenters anti-ddoses fail even vs. very weak attacks), but not from website DDoSes (OVH fails on website DDoSes too).
You are running XAMPP (A after X is for Apache web server).
It's like saying DoS/DDoS me with anything,
can be - first Google result - Ataki Slow HTTP DoS (cz. 1.) – Slowloris (https://sekurak.pl/ataki-slow-http-dos-cz-1-slowloris/) (yes, it's 2014 post and XAMPP still cannot handle this attack).
It's first attack in Google, but you can easily find 10 others. All of them will turn off web server, some of them will turn off whole VPS.
Google's 3rd result is OTLand's post about XAMPP and it already mentionednginx- Apache replacement, easy to install on Linux - in 2012 Xampp - ataki (https://otland.net/threads/xampp-ataki.175332/) (https://www.google.com/search?q=xampp+slowloris).
I've never DDoSed any OTS and I'll not change it to prove that your VPS can be taken down with 4 (or 1) lines of Bash (Linux) script in console on home 1 mb/s internet connection.
Ready to run Python script [much longer, but also easily configurable]: GitHub - gkbrk/slowloris: Low bandwidth DoS tool. Slowloris rewrite in Python. (https://github.com/gkbrk/slowloris)
CREATE TABLEcharacter_sale(
idint(11) NOT NULL,
from_accint(11) NOT NULL,
char_namevarchar(255) NOT NULL,
char_idint(11) NOT NULL,
keyvarchar(255) NOT NULL,
priceint(11) NOT NULL,
processedtinyint(1) NOT NULL DEFAULT 0
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;