roriscrave
Advanced OT User
- Joined
- Dec 7, 2011
- Messages
- 1,210
- Solutions
- 35
- Reaction score
- 206
Recently a person contacted me, and said that he can take down the site of 95% of the otlist servers.
He took down my site and took down some other sites to prove to me that he could do it.
And is asking for money for give a 'possible solution'
he said he brought this Ddos from other mmorpgs (he calls it a proxy).
even websites with cloudflare are down, I will send some information below.
1) He attacked a server with +- 800 players online and cloudflare (https://ntoultimate.com.br/)
error in website during attack:
2) He attacked a server with +- 1000 players online and cloudflare (otPokemon Jogar Pokémon Online MMORPG (https://otpokemon.com/))
error in website during attack:
3) he tried to attack kasteria.pl and was unsuccessful
4) the photo he sent me of how he attacks the site:
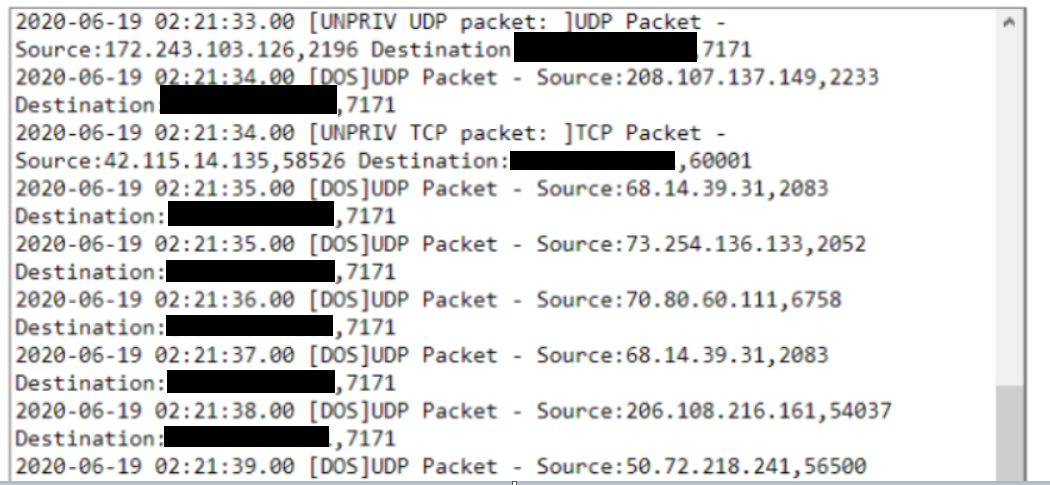
5) when he attacked my website, i used this command in linux to check all conections, and oddly enough, the ip that was attacking me was 127.0.0.1 (localhost)
obs: he took down the site of several servers, sites in gesior, znote and myacc.
He took down my site and took down some other sites to prove to me that he could do it.
And is asking for money for give a 'possible solution'
he said he brought this Ddos from other mmorpgs (he calls it a proxy).
even websites with cloudflare are down, I will send some information below.
1) He attacked a server with +- 800 players online and cloudflare (https://ntoultimate.com.br/)
error in website during attack:
2) He attacked a server with +- 1000 players online and cloudflare (otPokemon Jogar Pokémon Online MMORPG (https://otpokemon.com/))
error in website during attack:
3) he tried to attack kasteria.pl and was unsuccessful
4) the photo he sent me of how he attacks the site:
5) when he attacked my website, i used this command in linux to check all conections, and oddly enough, the ip that was attacking me was 127.0.0.1 (localhost)
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nobs: he took down the site of several servers, sites in gesior, znote and myacc.