.: Strike :.
Active Member
- Joined
- Mar 8, 2008
- Messages
- 22
- Reaction score
- 26
Download for Windows and macOS: https://www.wireshark.org/download/automated/, On Linux you'll have to compile current Wireshark master branch yourself till there's an official release (Summer 2018). See here for more info.
Wireshark is a very popular network analyzer. It sniffs what happens on your network and attempts to display it in text form:
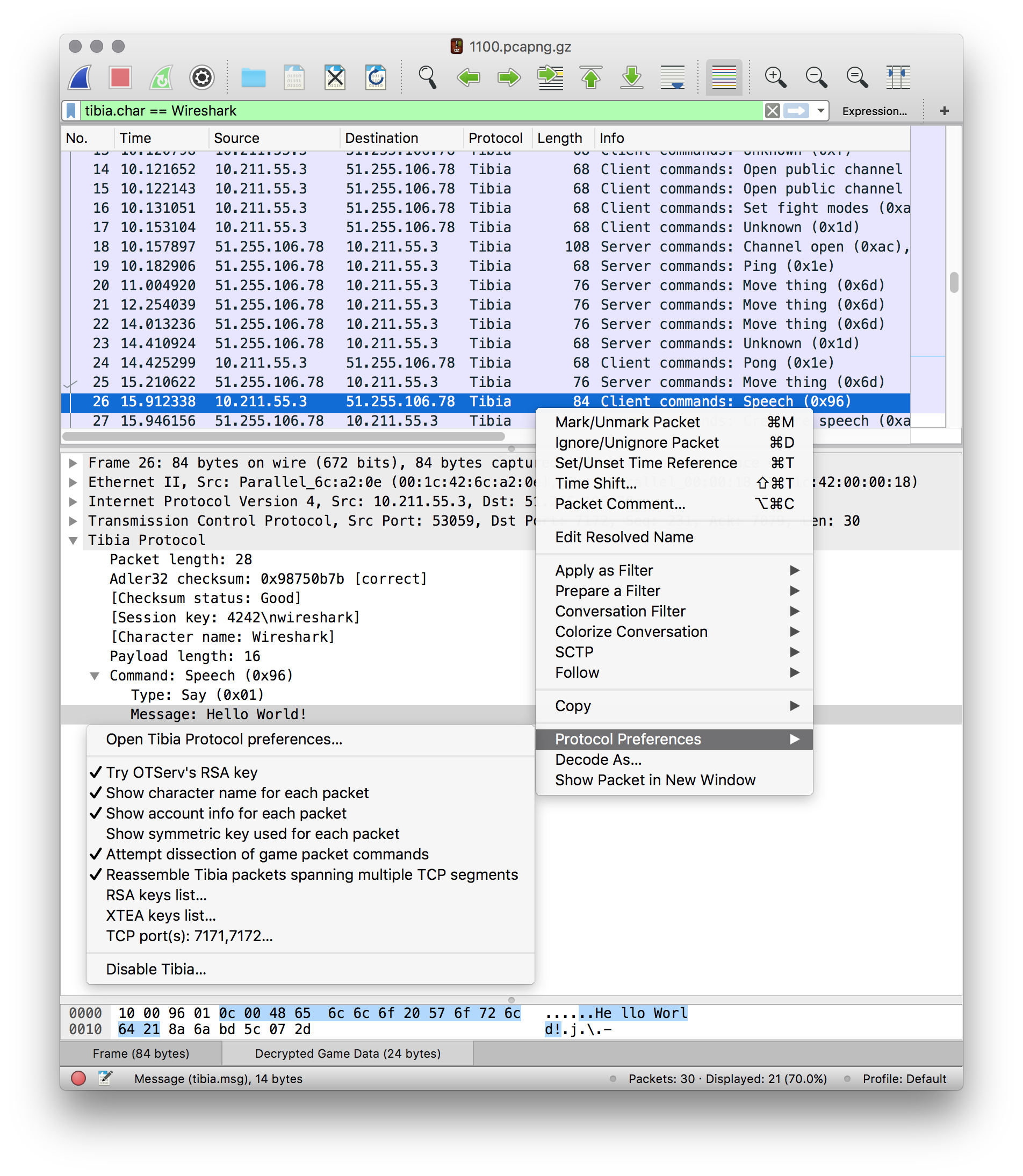
And now it has Tibia support. So you can, in theory[1], start up any Tibia client from 7.0 to the current one and see in real-time what messages it exchanges with the server it connects to.
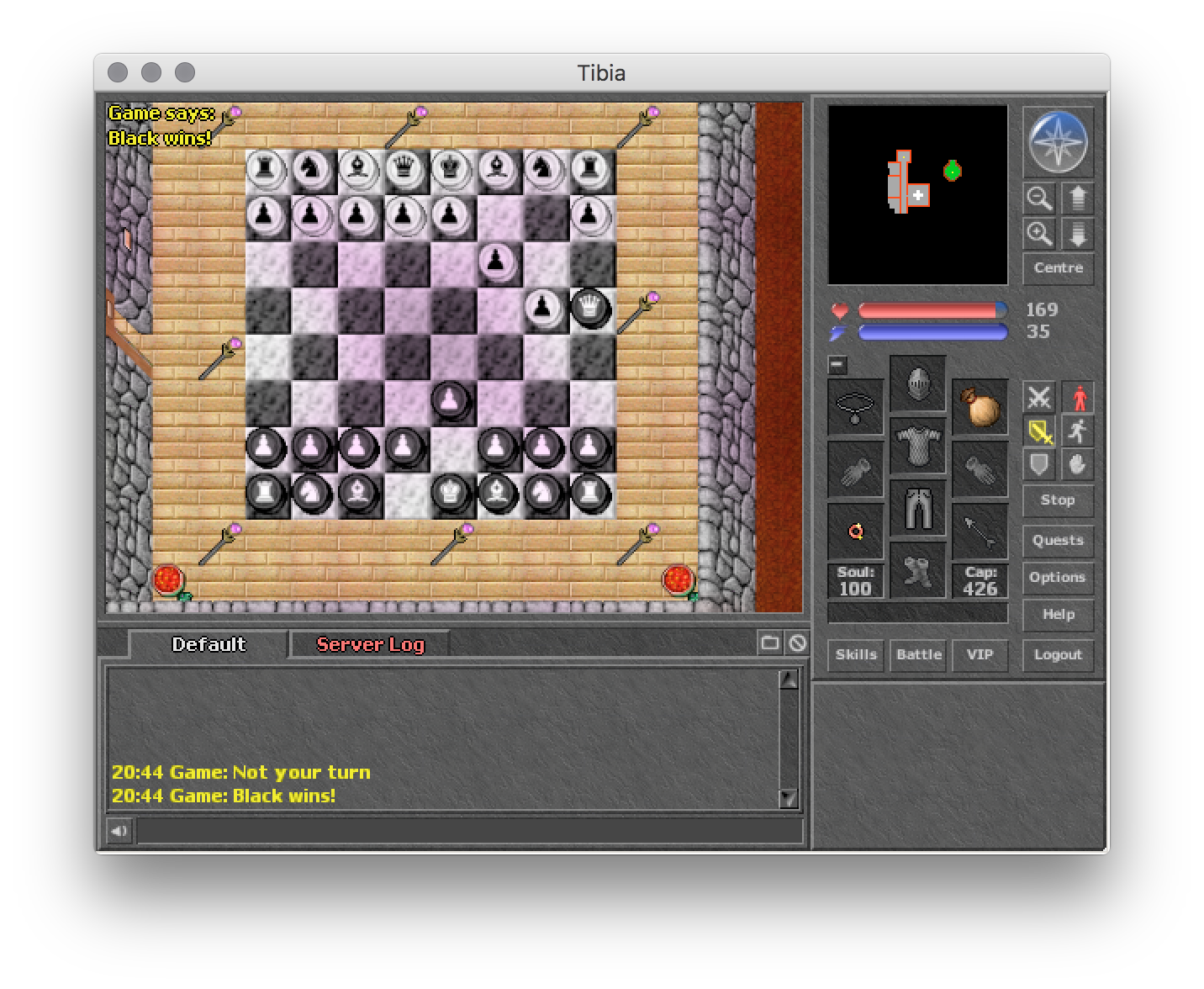
What can you do with it? It helped me turn a Tibia client into a chess client:
I've used it to analyze bugs exploited by players on a closed-source OTServ. And to analyze mage bot logins in order to block them.
I hope it makes the barrier of entry for custom Tibia tools lower, write your own custom Tibia server, write a bot for a locally hosted OTServ to learn more about algorithms or analyze what your Tibia client sends to the server and maybe make a loot HUD? You can decide yourself what you want to build with it!
You can easily extend Wireshark dissectors with your own Lua scripts, so you could offload sniffing, key-handling and decryption to Wireshark and write a Lua script that does something with the game commands.
A brief overview of the dissector and the protocol is given here:
Tibia-Wireshark-Plugin/packet-tibia.c at wireshark-merge · a3f/Tibia-Wireshark-Plugin · GitHub
[1]: Tibia is encrypted since 7.7. You would need to supply a XTEA key only you and the server know while you are logged in or a private key only the server has to decrypt the packet. Most OpenTibia servers use the same private key, which is therefore no longer private and can be analyzed directly now in Wireshark. Otherwise, you can supply the session key and dissect even real Tibia traffic.
Wireshark is a very popular network analyzer. It sniffs what happens on your network and attempts to display it in text form:

And now it has Tibia support. So you can, in theory[1], start up any Tibia client from 7.0 to the current one and see in real-time what messages it exchanges with the server it connects to.
What can you do with it? It helped me turn a Tibia client into a chess client:

I've used it to analyze bugs exploited by players on a closed-source OTServ. And to analyze mage bot logins in order to block them.
I hope it makes the barrier of entry for custom Tibia tools lower, write your own custom Tibia server, write a bot for a locally hosted OTServ to learn more about algorithms or analyze what your Tibia client sends to the server and maybe make a loot HUD? You can decide yourself what you want to build with it!
You can easily extend Wireshark dissectors with your own Lua scripts, so you could offload sniffing, key-handling and decryption to Wireshark and write a Lua script that does something with the game commands.
A brief overview of the dissector and the protocol is given here:
Tibia-Wireshark-Plugin/packet-tibia.c at wireshark-merge · a3f/Tibia-Wireshark-Plugin · GitHub
[1]: Tibia is encrypted since 7.7. You would need to supply a XTEA key only you and the server know while you are logged in or a private key only the server has to decrypt the packet. Most OpenTibia servers use the same private key, which is therefore no longer private and can be analyzed directly now in Wireshark. Otherwise, you can supply the session key and dissect even real Tibia traffic.
